What is best for application security testing: SAST, DAST, or SCA
With a 43% rise in data breaches tied to web application vulnerabilities according to Verizon, enterprise security teams are looking more closely at how security controls can be integrated to DevOps without impacting productivity. But with so many automated security testing tools (SAST, DAST, SCA) on the market, it’s important to understand the difference and when to use them to ensure robust Application Security.
DevOps is an integral part to any business as the development team deliver new products to the end user and help drive revenue, therefore the focus is often on speed and quality, not security. However, with a sharp rise in application layer attacks, enterprises must work to reduce security issues in the development process to prevent costly data breach from affecting customers down the line.
The introduction of DevSecOps helps security professionals understand how they can successfully integrate security in an automated way that doesn’t slow down development while allowing DevOps to focus on what matters most – building and creating. In this blog we’ll explain the different automated application security testing tools that are commonly used in the agile development cycle, and when you should use them to ensure a secure Software Development Life Cycle (SDLC).
Understanding the difference between SAST, SCA and DAST
The most popular application security testing tools businesses implement in their development cycles are Static Application Security Testing (SAST), Software Composition Analysis (SCA) and Dynamic Application Security Testing (DAST). Knowing the differences and when to use them is crucial to enhance your DevSecOps.
Static Application Security Testing (SAST)
As development speed increases and DevOps embrace new agile methodologies and technologies, integrated static analysis within the CI/CD pipeline can help detect vulnerabilities early in the software development process from the inside out (white box testing). The benefit of a SAST solution is it doesn’t require a running system to perform code security checks and won’t slow you down like a manual code review or penetration test.
SAST automatically checks for vulnerabilities within the application source code, byte code, or binaries line-by-line, ensuring security weaknesses such as those listed in the OWASP Top 10 and the 2019 CWE Top 25 in the proprietary code are detected from the start, during development. Allowing developers to identify the risks and fix any vulnerabilities before they can make it into production. This way, developers are empowered to shift left and recognize early code defects in the development cycle with security best practice.
Advantages of SAST:
| Disadvantage of SAST:
|
Dynamic Application Security Testing (DAST)
Unlike SAST, Dynamic Application Security Testing (DAST) is done from the outside looking in (black box testing) and identifies vulnerabilities when the application is already running.
DAST tools crawl web pages, locate endpoints of web services, inputs and outputs therefore requiring a working version of a web application for the testing to work. Without looking into the source code, dynamic analysis works to simulate penetration testing like attacks to uncover exploitable vulnerabilities and business logic issues from a hacker’s point of view, with reliable results.
But since the scanning happens towards the end of the SDLC (running applications), the findings can be substantial and often put pressure on DevOps to fix these runtime vulnerabilities quickly, creating friction between the security and development teams.
Advantages of DAST:
| Disadvantage of DAST:
|
Software Composition Analysis (SCA)
Getting new features out to market fast, almost always means developers don’t write all of their own code. The use of packaged open-source code is commonplace in modern DevOps and so is the need for security governance. With some SAST solutions now including Software Composition Analysis (SCA) to boot you need to understand how they work together to locate weaknesses in proprietary code and vulnerabilities in open-source code.
SCA tools analyze the open-source component by detecting software licenses, deprecated dependencies as well as known vulnerabilities and potential exploits in a codebase, enabling DevOps to manage their security exposure and license compliance. In addition, composition analysis can be run and expanded to newer architectures including containerized environments to automate detection for publicly disclosed vulnerabilities within your containers and those disguised in public registries (Docker Hub) being brought into the project.
With open source components now present in 96% of commercial applications, the ability to spot software supply chain vulnerabilities in development, in and out of the cloud, are vital to reduce application risks – all of which can be a potential entry point for malicious actors as we’ve learned from the Equifax breach.
Choosing the best application security testing tools
As we’ve shown in this blog, there are plenty of options available for addressing application security risks in the CI/CD pipeline, creating a real head-scratcher to know what’s best to protect your applications. Therefore, it’s important to understand how each Application Security Testing (AST) tool should be used across the development lifecycle to optimize your application security controls.
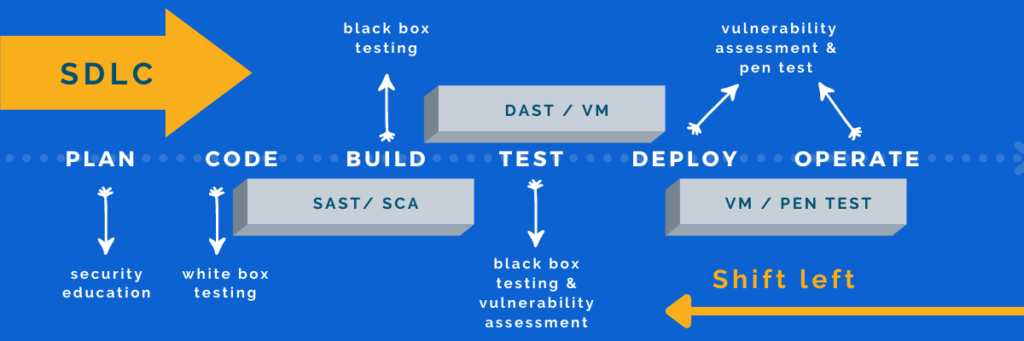
The next step is to align application security testing with your development model:
Outsourced development and Commercial-off-the-shelf Applications (COTS): COTS/outsourced development offers enterprises cost efficiency and a more convenient way to fulfil business needs without developer overheads and the need to create apps in house from scratch. However, can you trust the software vendor or development partner that everything is secured before it reaches you? When it comes to critical business applications, black box testing is advised for enhanced security peace of mind. Without access to the source code, DAST scanning and/or penetration testing are ideal to test the running application for any critical software vulnerabilities before deployment and to monitor security compliance in the long run.
Internal development and software customization: For businesses who have the resources and infrastructure to create applications in house it’s important to build security testing into the SDLC from the beginning to protect you against application vulnerabilities including Cross Site Scripting. For true DevSecOps arm your development teams with SAST/SCA tools to ensure code security in the ‘code and build’ stage and apply black box testing (DAST) for security assurance before deployment. Once deployed, regular pen testing and vulnerability assessment of the infrastructure that it runs on are also recommended to keep security issues in check with each new release.
Improve your application security today
With cyber-attacks against web services businesses increasing at an alarming rate and opportunistic hackers using every technique in the book, it’s important for organizations to have complete application security across the SDLC. Providing maximum security coverage for your development and ensuring they can deploy safely with the same speed and confidence for your business success. Talk to us today and see how our suite of application security testing tools can help ensure a successful security integration for your DevOps.